Information Security
Our Information Security Services combine our extensive experience and knowledge to address your security requirements. We are flexible in our approach. Our methodology combines our multi-industry, regulatory, technical experience, knowledge, and professional certifications.

Features
Our services cover all aspects of information security and include, but are not limited to evaluating and providing remediation in the following areas:
Assess Strategy
Customize a security strategy and policy to your organization.
Assess Risk
Assess enterprise risk and regulatory compliance to address gaps, manage risk and allocate resources to better protect your organization.
Assess Threats
Provide threat and vulnerability management services help determine threats, their root cause and remediate these vulnerabilities.
Managed Services
Provide information security services that are designed to become an extension of your security staff.
Assess Architecture
Assess your current security architecture and recommend solutions, methodologies and leading practices to reduce risks to your environment.
Provide Training
Provide education and awareness services to ensure a more secure environment.
Risk Factors
Events, Threats and Weaknesses
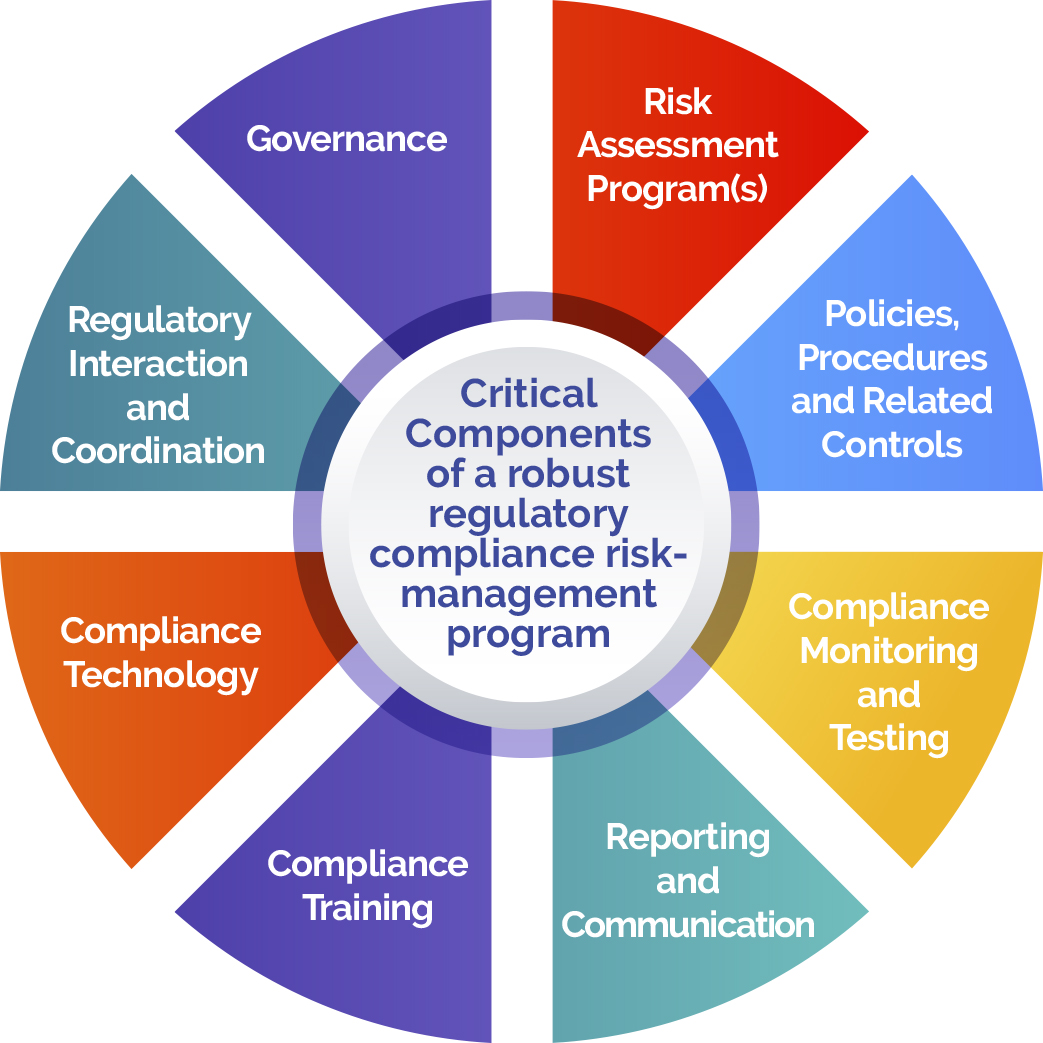
Our approach considers the following risk factors, including those noted within other risk frameworks:
- Changing governance and regulatory reporting environment.
- Materiality, including a consideration of the dollar value and the volume of transactions as well as the complexity of the underlying processes.
- The perception of control effectiveness, including the consideration of management’s regard for effective control, the existence and effectiveness of policies and procedures, and the results of past audits and compliance reviews and assessments.
- Organization reputation and image preservation.
- Inherent risks that have a certain level of impact and likelihood without consideration of existing risk responses and control activities.
- The level of change and the resulting impact to systems, processes, procedures, people, and the organization – as a whole.
- Industry/market trends and other inherent control issues.
Assessment of Risks
Each process and risk are assessed based on the following:
- We identify relevant risks, based upon industry expertise, management and our experience and knowledge.
- For each risk, we discuss with management any mitigating factors the organization has implemented to mitigate the respective risk.
- Based upon the perceived strength or weakness of those mitigating factors, we assign each risk a net risk ranking.
We define processes as having a High, Medium or Low risk ranking as follows:
- High/Extreme Likelihood and Impact – Those risks that are likely to occur within a certain or imminent time horizon; such risks will cause organizational objectives to be jeopardized, which could potentially harm the organization in a financial or operational manner.
- Medium Likelihood and Impact – Those risks whose likelihood of occurring within a defined time horizon is more than remote; such risks will cause some element or component of organizational objectives to be delayed or not achieved or whose result could cause more than an inconsequential financial or operational impact.
- Low / Minor Likelihood and Impact – These risks are viewed as unlikely to occur within a reasonable timeframe; such risks will not substantively hamper the achievement of organizational objectives.
All Our IT Services
Contact Us Today!
Once experiencing our work, you will find what our clients have found...That there is no need to look elsewhere for quality services for your assurance and advisory practice.