Cyber Security
Our Cybersecurity team combines extensive experience and knowledge to address the cyber threat landscape to protect your organization from escalating threats. We are flexible in our approach. Our methodology provides actionable steps to secure systems more effectively and provide recommendations to improve compliance with a wide variety of regulatory frameworks.

Features
Cybersecurity services include, but are not limited to evaluating and providing remediation in the following areas:
Meeting regulatory requirements
Examples include: FFIEC, State, HIPAA/HITRUST.
Threat and Vulnerability Management
Uncover and remediate flaws and vulnerabilities in your security systems.
Security Architecture and Implementation
Helps you make decisions about the right technology, architecture and projects to ensure enterprise and network security.
Vulnerability Assessments
Identify, quantify and rank vulnerabilities based on the risk they pose.
Adherence to accepted frameworks
NIST, ISO 27001.
Enterprise Risk and Compliance
Better understand risk through an IT risk assessment and make informed decisions about managing it.
Penetration Testing/Social Engineering
Where our security experts attempt to breach the information security controls of your organization using the same tools and techniques that real-world attackers employ.
Solution Highlight
Vulnerability Assessment Workflow
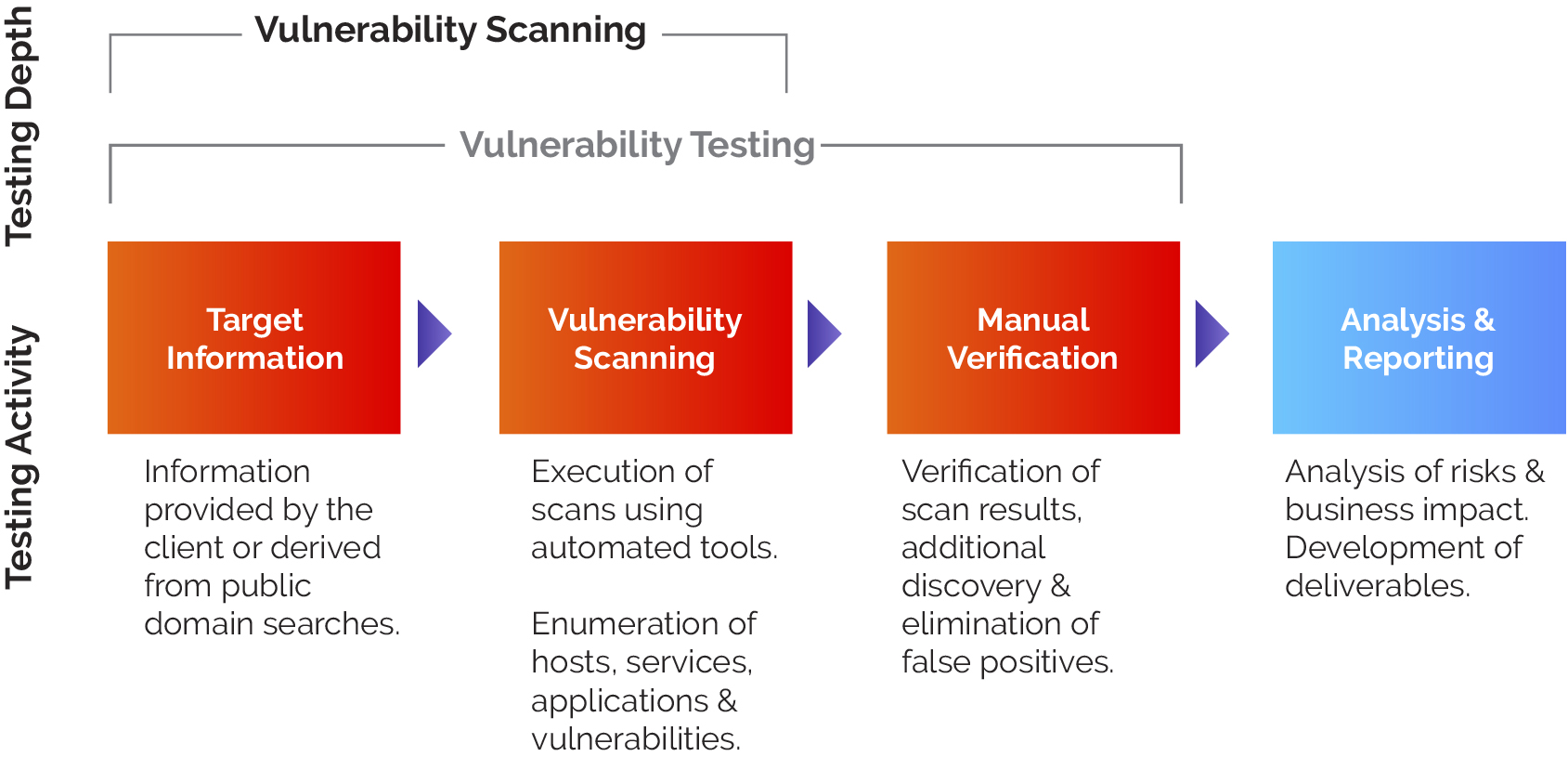
Step 1
- Utilizing publicly available information and non-intrusive reconnaissance procedures, eDelta will perform a discovery of your organizations public external IP addresses, and then reconcile these to the actual external IP address range provided by your organization.
- Perform vulnerability scans on external address ranges and provide reporting of vulnerabilities identified and services running on discovered external public facing devices.
- Testing will be performed at your organization’s office.
- Perform a retest of any high-risk vulnerabilities will be performed if needed.
Step 2
- Using the information obtained in from Step #1 perform a penetration test of servers and network devices and provide a report of exploited vulnerabilities identified.
- A retest of any exploited vulnerabilities will be performed if needed.
Services
eDelta will evaluate and classify each potential risk and vulnerability into the following categories:
False Positive
Scanning tools report vulnerabilities when certain conditions exist. Those conditions, however, in certain situations and configurations, do not pose vulnerability. Hence, the classification of “false positive” is warranted.
Accepted Risk
Certain vulnerabilities present low risk because the risk of exploitation is low and the impact, if exploited, is low, etc. These vulnerabilities and the related risks can be “accepted” by management and receive this classification.
Mitigated Risk
Remediation Required
All Our IT Services
Contact Us Today!
Once experiencing our work, you will find what our clients have found...That there is no need to look elsewhere for quality services for your assurance and advisory practice.

